HTB — Previse Walkthrough

Step 1 — Port Scanning / Reconnaissance

The initial NMAP scan only revealed two ports open, port 22 (SSH) and port 80 ( HTTP). Let’s visit the website.

I checked out the source code, but I didn’t really find anything, so I ran a Gobuster to start fuzzing the site for hidden directories.

Gobuster returned a lot of great results, but the most important one is nav.php.
We want to focus on “accounts” since the website is locked on the front end and whenever you click on these links it will redirect you to the login page. We need an account to further footprint the website.

I decided to look at the request being sent by using Burp Suite to intercept the request via Foxy Proxy.
Step 2— Burpsuite & Bypassing Login Page

Let’s look at connection which says close. I would like to see the response. Let’s select Response to this request.

I changed the status code to 200 to indicate a success then hit Forward.

It worked! I then made a new account with my name and password then hit create user.

Step 3— Login & Exfiltration of Site Data

I used my credentials to login.

I looked around a bit and found that there was a site back up file available, so I downloaded it to see what was inside.
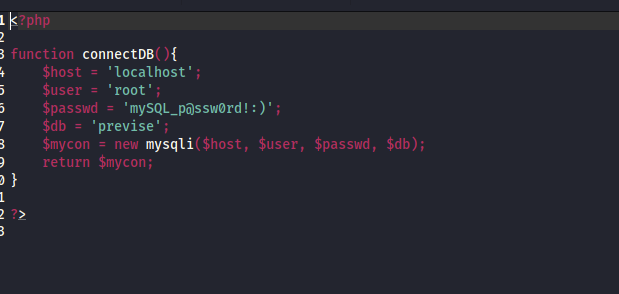
In the config file there was the SQL Password & Username. I saved that on my notepad for later.

From my web dev days, I knew how risky it was was to use a delim, because you could change it via the inspector tool or even using Burp Suite and insert commands, like a reverse shell. In this case, the delim is the submit button.

First, I set up my netcat listener. Then I used Burp Suite to intercept the request and change it to make the request open a reverse shell on port 4444. I set up my listener than forwarded the request.

Step 4— Reverse Shell and SQL Table Enumeration

I had my netcat listener running on port 4444 while I was using Burp Suite to send over a reverse shell command via the delim vulnerability. I got in and spent a good amount of time peeking around the www-data account. Couldn’t find anything interesting, so I used the SQL login I found earlier appending it with -e ‘show databases;’ to see what I could find.
I saw a database named Previse, so I then hit the same command but asked it to show tables to see if I could see some accounts. I then did a select * from accounts to dump the username and hashes. The user m4lwhere was there, so I copied that down on my notepad. I still needed to figure out what the hash was encrypted in. So I returned to the site backup download file.
Step 5— Password Cracking

In the accounts page of the site back up, you can see that crypt is the hash type.

I then used John and the Rock You wordlist with the format being md5crypt-long to crack his hash. It took about 7 minutes.
Step 6— Login as User & User Flag

I used the credentials that I got from John and logged in as the user via SSH. The user flag was in the initial directory. We still needed to get the system flag. I ran sudo -l to see if m4lwhere was able to run anything as root and seems like he was able to run this backup script. Let’s check it out.
Step 6 — Privilege Escalation and System Flag

When I looked at this shell script in nano, it seemed like this script was used to access backups. Let’s head over to the tmp file directory to see if we can create a file called Gzip.txt as an executable.
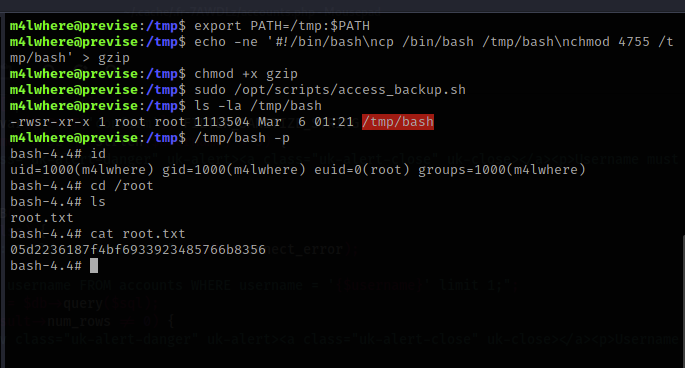
First I exported the gzip file path into the directory. I then created the bin bash command into a txt file. I then changed it to an executable file so that when I run access_backup.sh that it will execute. I then ran the script. Then I set the UID to root by executing bash with the -p flag and I was able to acquire the system flag and root the box.
Thanks for Reading!